We had a malware recently that manifests itself in creating shortcuts in mapped network drives and then hides all the real files in the drive and leaves only fake shortcuts in their place. This is our understanding of the malware and what it does and how to stop it.
Malware on users computer
![]()
When we checked the users computer that had first reported the shortcuts appearing in their mapped network drives we used several Anti Virus providers to scan the disk and all of them returned no malware found. So we turned to the trusted AutoRuns application that shows you everything that runs on start up on your computer and this found the pictured file. What we have here is an EXE that exploits a Flash Plater vunerability and then installs into the users AppData folder so that it has the necessary permissions to execute. Now in this example I have obsfucated the actual URL of the site that has the Flash exploit installed, but the malware leaves the URL in the folder structure so you can see the site that caused the drive by download.
The location is C:\users\%username%\appdata\roaming\macromedia\flash player\#sharedobjects\girh2t5n\www.urlofsite.co.uk\ptvflash\flii\slui.exe
Malware Payload
![]()
The malware itself when executed will create a file called thumbs.dbh in each mapped drive and then execute itself to create the shortcuts and hide the real files by changing the attributes.
Thumbs.dbh
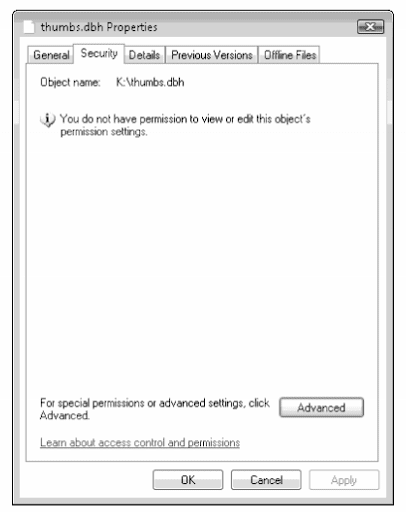
Now a big part of the issue with this malware is how to stop it while you check each computer and patch Flash Player, what we did was to create our own file called thumbs.dbh in the root of each mapped drive and then set the permissions to deny to all users. What this does is allow the malware to think it can work and it tries to call the thumbs.dbh file each time is deploys, but it fails because the file has deny access to everyone. This means the malware is active but cannot deploy the payload and therefore you have time to update Flash Player, Java and Windows Updates and then once all computers are updated you can remove the original malware in AppData and then fake thumbs.dbh file that we created.
No comments:
Post a Comment